How Do Directory Services Provide Access Control
A directory service is a database for storing and maintaining information about users and resources. Directory Services are frequently referred to as directories, user stores, Identity Stores, or LDAP Directory, and they store information such as usernames, passwords, user preferences, information well-nigh devices, and more. Network and system administrators use directory services to onboard users, manage access privileges and monitor and control access to applications and infrastructure resource. For example, when a user accesses an awarding, that application volition reference the directory service to ensure the user is legitimate and has the proper privileges to access and use that application.
Directory services are primal elements of an Identity Security strategy. Many identity and admission management (IAM) solutions use directory services in conjunction with single sign-on (SSO), multi-factor hallmark (MFA) or identity lifecycle direction functionality.
Directory Services Elements
A directory service is normally implemented in software and distributed beyond multiple servers for scalability, performance and resiliency.
Enterprise directory services like Microsoft Active Directory provide:
- A schema that describes the various directory objects (eastward.k., user, server, printer) and their attributes (east.g., name, address, telephone number)
- A universal database or catalog containing detailed information about every object in the directory
- An index and query methodology for users, administrators and applications to retrieve information from the directory
- Replication functionality for disseminating directory data across distributed servers
- Peering functionality for federating directory services across different enterprises and namespaces
Directory Services in the Cloud Era
Microsoft Active Directory is past far the most widely adopted directory service in the business world. Active Directory was conceived to maintain data nearly traditional enterprise It implementations and risk boundaries. In a traditional IT environs, stationary role workers use company-owned devices to access resource and applications hosted in on-premises data centers.
Active Directory is not hands extended to the cloud-first, mobile-commencement era of IT where applications and users oft reside outside the enterprise network perimeter. In today's world, users access a diversity of SaaS solutions (e.one thousand., Salesforce, Google Workspace), Infrastructure-as-a-Service (IaaS) workloads (e.yard., virtual machines running on Microsoft Azure) and on-premises applications from any location, using any device (e.grand., company-owned, BYOD, mobile, etc.).
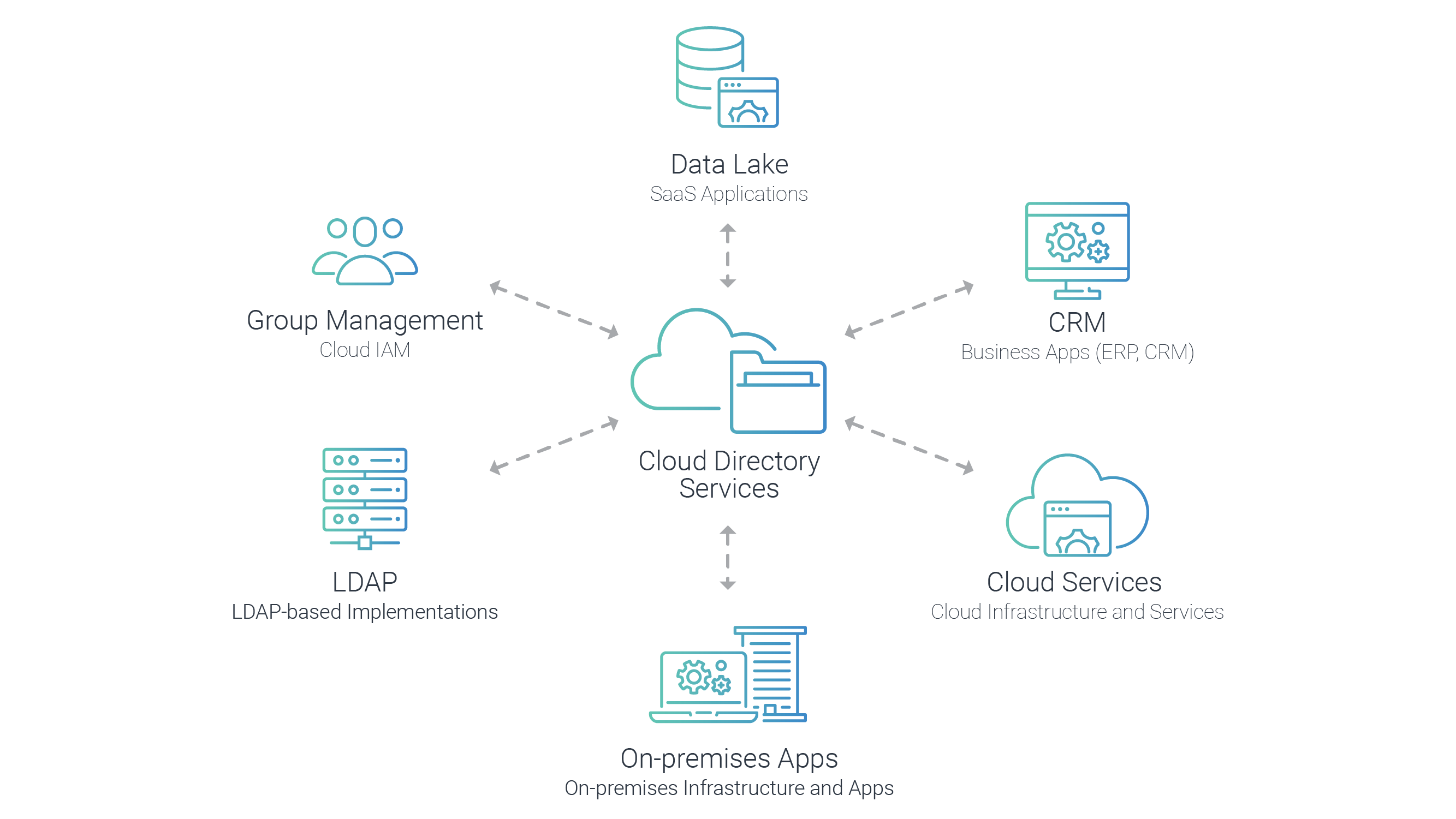
Many businesses are implementing virtual directories (sometimes chosen cloud directories) to support hybrid It environments and deject-axial users. A virtual directory aggregates and normalizes information from a diverseness of dissimilar on-premises directories (eastward.g., Active Directory, LDAP-based implementations) and cloud-based directories (e.g., Azure Agile Directory, Google Cloud Directory)—in real-fourth dimension. A virtual directory delivers a common framework and serves as an abstraction layer that decouples users and applications from the backend directory services for ultimate performance, scalability and extensibility. Virtual directories as well make information technology easy to securely manage to the lowest degree privilege admission across hybrid implementations.
Enterprises can use virtual directories for peering and federation and to enable unmarried sign-on across dissimilar applications and services. Nearly virtual directories support modernistic authentication protocols like SAML, OpenID Connect and OAuth, equally well as traditional authentication protocols similar Integrated Web Hallmark (IWA).
Virtual directories are typically delivered as office of IAM solutions and tin be deployed on-premises or in the cloud. In improver, leading Identity-every bit-a-Service (IDaaS) providers offer deject-based virtual directories.
Learn More About Virtual Directories
CyberArk Cloud Directory Services
- Forrester Wave™ Identity-Equally-A-Service (IDaaS) For Enterprise, Q3 2021
- CyberArk IDaaS Buyers' Guide
- Boosted Resources
How Do Directory Services Provide Access Control,
Source: https://www.cyberark.com/what-is/directory-services/
Posted by: carterancralows1973.blogspot.com


0 Response to "How Do Directory Services Provide Access Control"
Post a Comment